
Red Team vs Blue Team What's the Difference? Cyber Security Tutorial Simplilearn YouTube
For tech or cybersecurity pros looking to advance or try a new career, Red and Blue team engineers can have notably different salaries. A Red teamer currently commands a base salary of about $108,400 in the U.S., according to statistics from Glassdoor. A Blue team engineer, however, can expect a base pay of about $48,900, according to the same.
What is Red Team and How Does it Benefit Organizations? Sapphire
When it comes to red team vs. blue team, the former uses various methodologies, which often involve extensive reconnaissance to understand the target, followed by a series of attacks aimed at testing the organization's defenses. A crucial part of their operation is the "attack lifecycle," a model developed to simulate a full-fledged cyber.

Red, Blue, Purple, White, Black & Gold Team Privasec Global
The red team takes an offensive approach toward cybersecurity by mimicking hacker behavior, whereas the blue team acts more defensively to combat threats. This article breaks down the characteristics of red team and blue team members so you can understand how your skills fit into a cybersecurity career and answer the question, are you red team.

What is Red Team, Blue Team, Purple Team in Cybersecurity?
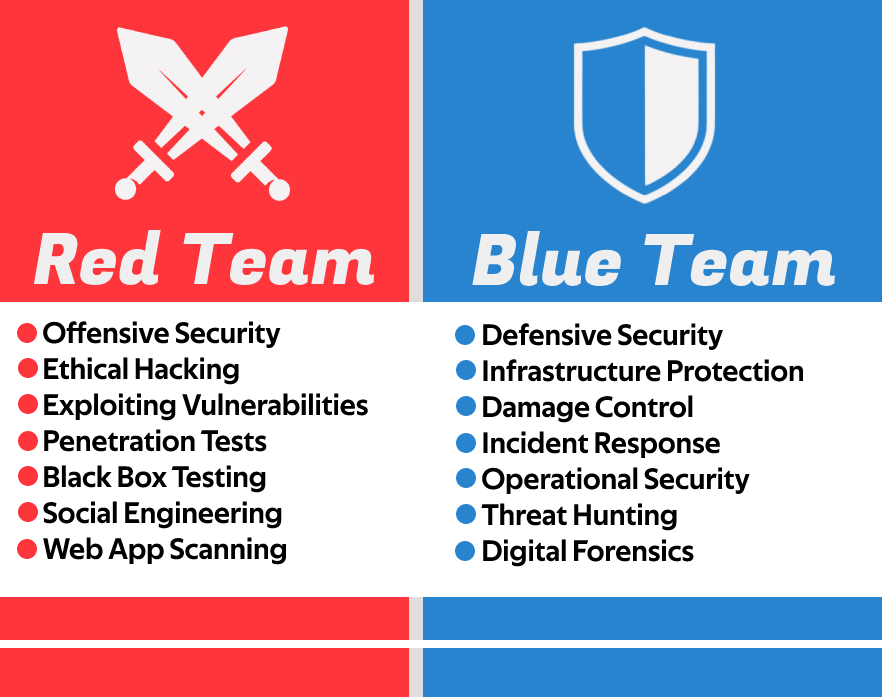
The red team is the offensive team in the security department, while the blue team plays defensive. A red team behaves like an attacker to break in, while the blue team is tasked with defending the organization from those attacks, including real-world attacks, and ensuring that every staff member is trained to be security-conscious and that they adhere to cybersecurity regulations.

Red Team Red vs. Blue Wiki Fandom
Zbigniew Banach - Wed, 13 Apr 2022 -. Red team versus blue team exercises simulate real-life cyberattacks against organizations to locate weaknesses and improve information security. The red team are the attackers attempting to infiltrate an organization's digital and physical defenses. The blue team's job is to detect penetration attempts.

Internal Testing A Comprehensive Guide ASTRA
Below, we'll tackle the three differences between the Red Team and the Blue Team for this engagement. 1. Pentesting Offense vs. Defence. Red vs. Blue pentesting is a simulated attack scenario in which the " Red Team " is the offense — their goal is to breach the cyber security defense in order to access company data or otherwise.

Red Team VS Blue Team แตกต่างกันอย่างไร และต้องมีความสามารถอะไรบ้าง EZGENIUS
The red team acts as an adversary and tries to infect the targeted organization's system with methods like malware and steal sensitive data. The blue team tries to minimize the chances of cyber intrusion and acts in defense when the red team tries to intrude into the security system. The drill that the red and blue teams perform helps to test.

Red Team vs Blue Team What’s The Difference? red team vs blue team cyber security Tecchy
The red team tries to get more power by finding weaknesses in the security defenses and start exploiting them to gain access to more system areas. They also attempt to steal sensitive data from the organization. But the blue team finds the points of attack, identifies the threats and takes action.

Team Blue vs. Team Red Club Penguin Wiki The free, editable encyclopedia about Club Penguin
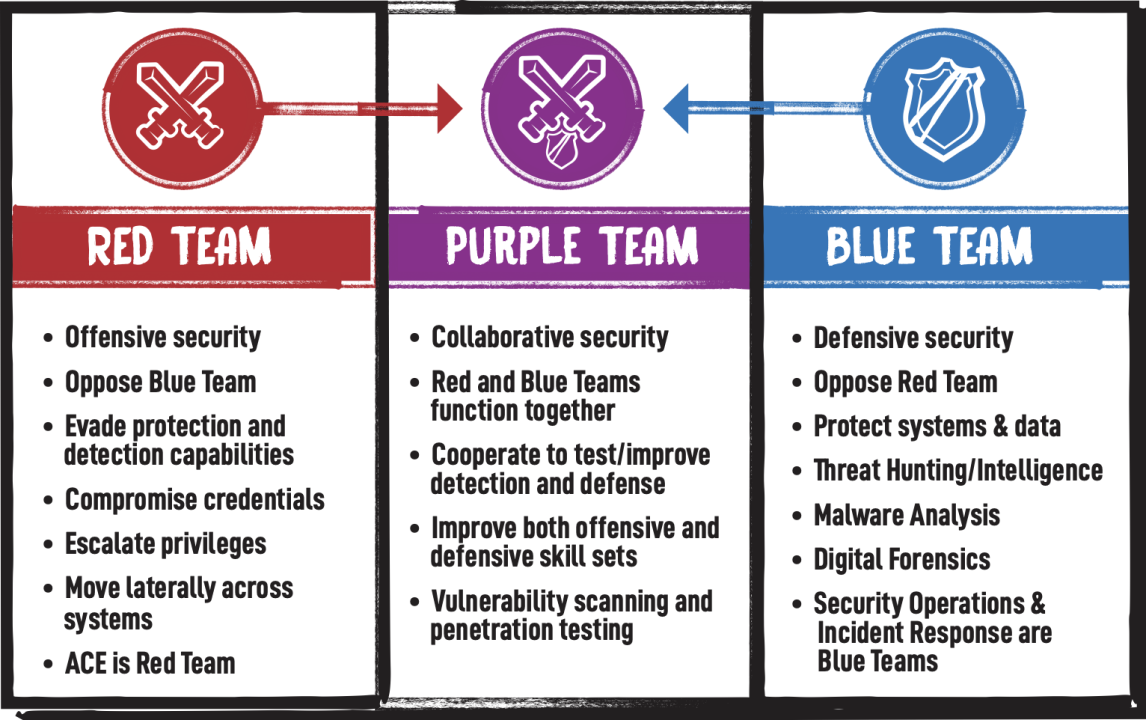
Calling the purple team a "team" is a bit misleading. The purple team is, in fact, not a standalone team but a mix of blue and red team members. While red and blue teams have the same goal of improving the security of an organization, too often both are unwilling to share their "secrets." Red teams sometimes will not disclose methods used to.
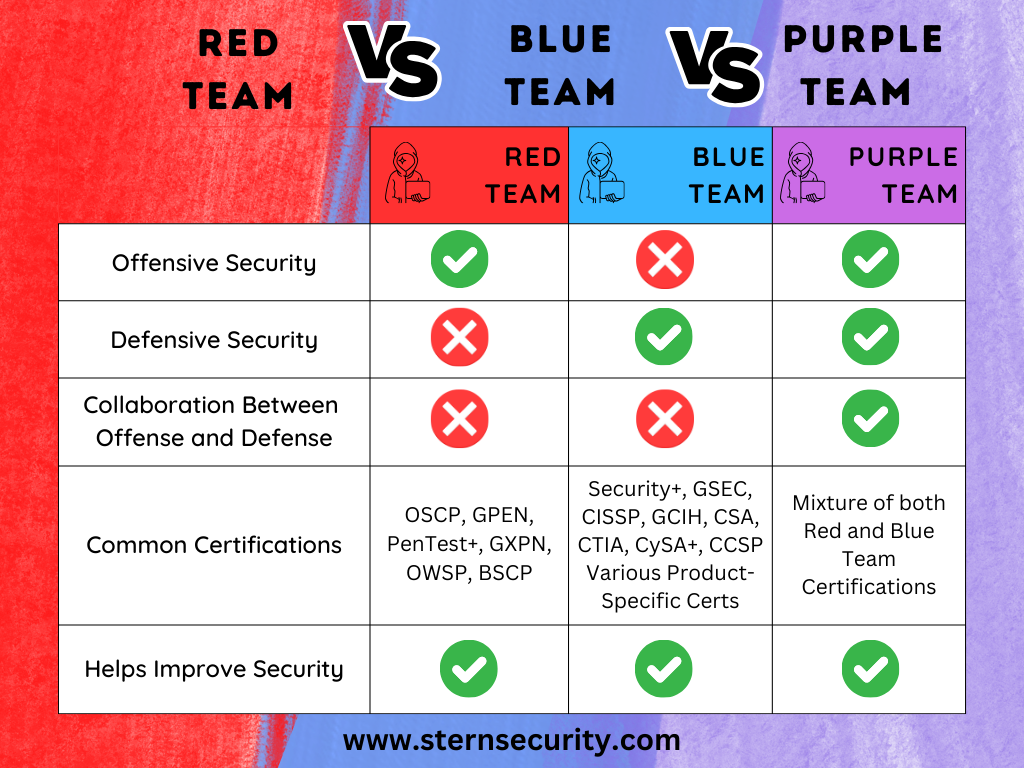
Red Team vs Blue Team vs Purple Team Cybersecurity Roles Stern Security
Red team/blue team exercises involve real-world simulated attacks in a controlled setting. The red team should try to breach defenses by techniques such as social engineering, exploiting vulnerabilities, and gaining unauthorized physical access. In contrast, the blue team should concentrate on detection, investigation, and response.
Red Team Vs. Blue Team InfosecTrain
Red teams are offensive security professionals who are experts in attacking systems and breaking into defenses. Blue teams are defensive security professiona.

RED TEAM VS BLUE TEAM ATTACKS
Both red teams and blue teams work toward improving an organization's security, but they do so differently. A red team plays the role of the attacker by trying to find vulnerabilities and break through cybersecurity defenses. A blue team defends against attacks and responds to incidents when they occur. In this article, we'll take a closer.

Red Team Vs Blue Team Understanding As A Service
The red team attempts to compromise the environment using real-world adversary tactics, while the blue team is made up of incident responders who work within the security unit to recognize, assess, and deal with intrusions. Red team/blue team simulations are crucial in protecting companies from a variety of attacks launched by today's highly.

Red Team and Blue Team Training ANY.RUN's Cybersecurity Blog
Red vs blue team exercises have since emerged as a crucial element of cyber resilience and security. Many businesses keep dedicated red and blue teams to ensure they're ready for potential breaches. In red vs blue team exercises, one team takes on the attacker's role while the other monitors and defends the network. The goal is to simulate.

One Team, Two Team, Red Team, Blue Team (And Also Purple Team) by Mackenzie Pech Medium
Red Team vs Blue Team Defined. In a red team/blue team exercise, the red team is made up of offensive security experts who try to attack an organization's cybersecurity defenses. The blue team defends against and responds to the red team attack. Modeled after military training exercises, this drill is a face-off between two teams of highly.
Red Teaming 10000 Feet
Red team cyber security assessments are a crucial way of giving organisations a practical understanding of their defence capabilities. In these exercises, the red team faces off against their counterparts, the blue team, in a battle to control a particular asset. That could be sensitive data, financial records, communication channels or the organisation's infrastructure itself. Assessments.
- Como Acender Cigarro No Carro
- O Q é Um Dorama
- Joao Paulo De Castro Ferreira
- Kaká Diniz E Filho De Abilio Diniz
- O Céu Estrelado De Van Gogh
- Como Fazer Carne De Porco De Lata
- Distancia Entre Navegantes E Balneario Camboriú
- Candidatos A Prefeitura De Fortaleza 2024
- Boku No Hero Academia Manga Online
- Cor Da Pedra Do Signo De Aquário