
¿Qué es un ataque Man in the Middle y cómo evitarlo? Servicios de Transformación Digital
28 Dec 2021 • 6 min. read. Man-in-the-Middle (MitM), que en español significa "hombre en el medio", es un tipo de ataque destinado a interceptar, sin autorización, la comunicación entre.

What is man in the middle attack ? How to protect from man in the middle attack ? YouTube
A man in the middle (MITM) attack is a general term for when a perpetrator positions himself in a conversation between a user and an application—either to eavesdrop or to impersonate one of the parties, making it appear as if a normal exchange of information is underway. The goal of an attack is to steal personal information, such as login.

Ataques "Man in the Middle” todo lo que necesitas saber Kymatio
A man-in-the-middle (MITM) attack is a type of cyberattack where attackers intercept an existing conversation or data transfer, either by eavesdropping or by pretending to be a legitimate participant. To the victim, it will appear as though a standard exchange of information is underway — but by inserting themselves into the "middle" of the conversation or data transfer, the attacker can.

ATAQUE MANINTHEMIDDLE Nivel 13 Ciberseguridad
A man-in-the-middle (MITM) attack is a type of cyberattack where a third party secretly places themselves in the middle of a data transfer or conversation between two parties. For example, MITM attacks often target banking websites — you think you're securely interacting with your bank, but a hacker is actually logging all of your.

ManintheMiddle Attacks explained, defined
The man in the middle. The intended recipient or application. One person - the victim - sends sensitive data online, such as an email. Then, there is an intended recipient - an application, website, or person. Between them, we have the "man in the middle.". This is the malicious actor who finds vulnerabilities, allowing them to watch.

¿Qué es un ataque Man in the Middle (MitM)? (Y Cómo Prevenirlo)
abril 13, 2022. Un ataque Man-in-the-Middle (MITM) es un tipo de ciberataque en el que los criminales interceptan una conversación o una transferencia de datos existente, ya sea escuchando o haciéndose pasar por un participante. A la víctima le parecerá que se está produciendo un intercambio de información normal, pero al introducirse en.
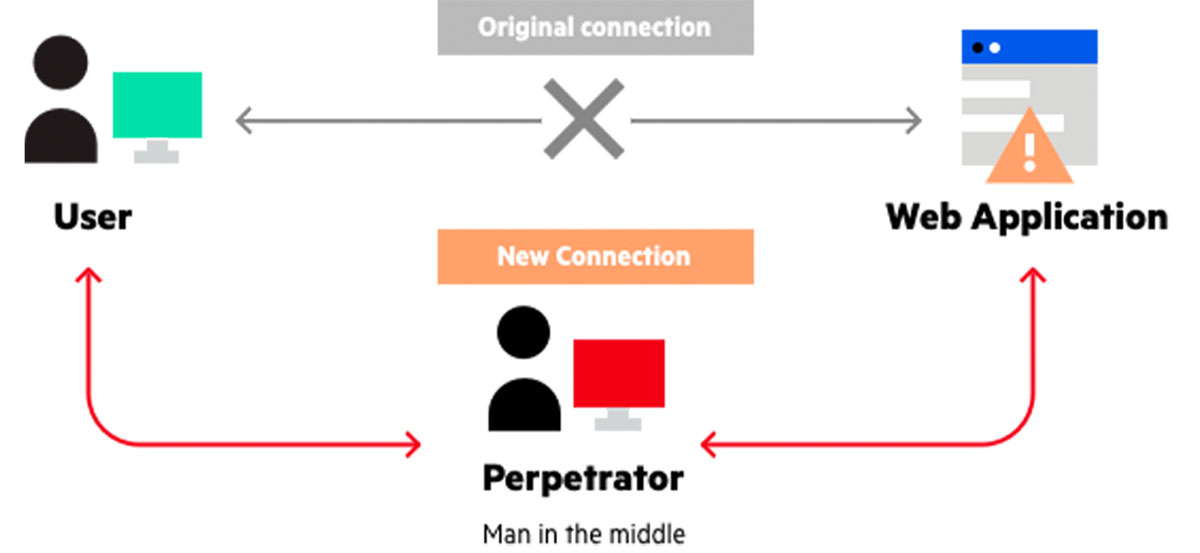
Ataque Man in The Middle (MITM), ¿qué es? Rincón de la Tecnología
Run your command in a new terminal and let it running (don't close it until you want to stop the attack). arpspoof -i wlan0 -t 192.000.000.1 192.000.000.52. As you can see, it's the same command of the previous step but we switched the possition of the arguments. Till this point you're already infiltrated to the connection between your victim.

Ataques 'Man in the Middle' cómo detectarlos y prevenirlos
Estos ataques son realmente efectivos y, a su vez, muy difíciles de detectar por el usuario, quien no es consciente de los daños que puede llegar a sufrir. Definición de ataque Man-in-the-Middle. El concepto de un ataque MiTM es muy sencillo. Además, no se limita únicamente al ámbito de la seguridad informática o el mundo online.

Maninthemiddle entenda o ataque e saiba como se proteger Backup Garantido
Man-in-the-middle attack. In cryptography and computer security, a man-in-the-middle [a] ( MITM) attack, or on-path attack, is a cyberattack where the attacker secretly relays and possibly alters the communications between two parties who believe that they are directly communicating with each other, as the attacker has inserted themselves.
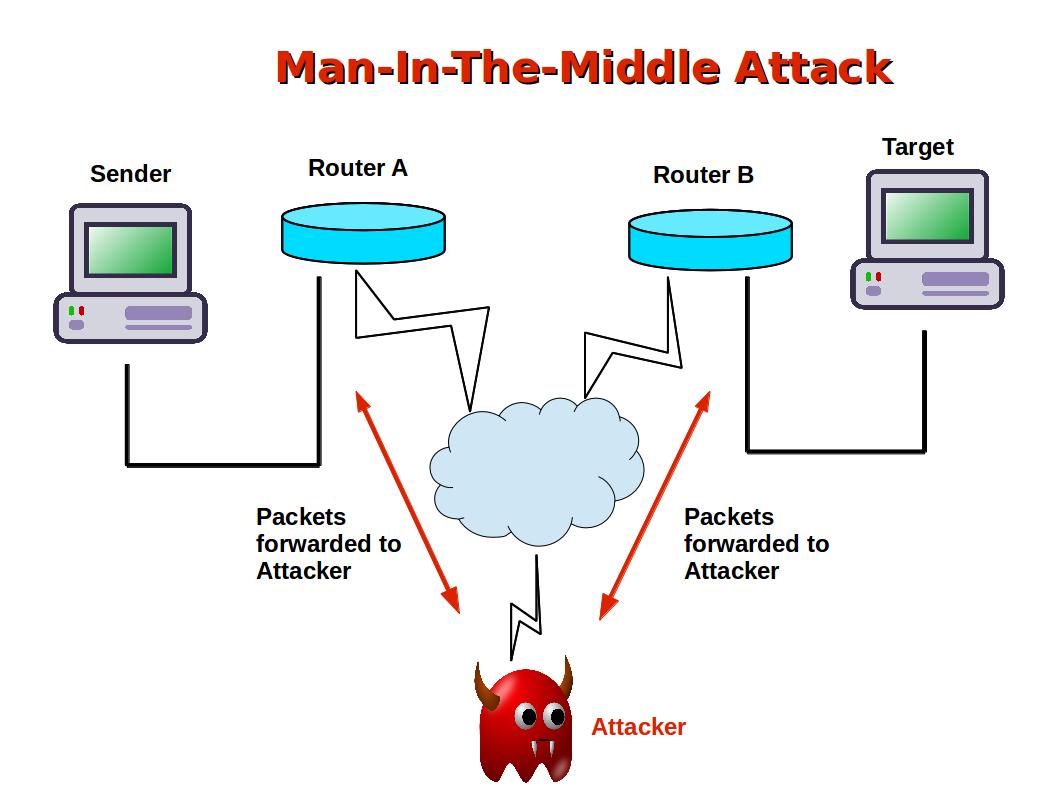
Computer Security and PGP What is a ManInTheMiddle Attack
El ataque Man in the Middle (MITM), del inglés "hombre en el medio", es un tipo de ciberataque mediante el cual los delincuentes espían las comunicaciones entre dos o más dispositivos.A través de programas informáticos y utilizando técnicas de engaño para que los usuarios se conecten a redes comprometidas, los malos consiguen colarse en el tráfico de datos y ver toda la.

Ataque "Man in the Middle" ¿qué es, cómo funciona y cómo protegerse?
In a man-in-the-middle attack, a black hat hacker takes a position between two victims who are communicating with one another.In this spot, the attacker relays all communication, can listen to it, and even modify it. Imagine that Alice and Barbara talk to one another on the phone in Lojban, which is an obscure language.Nancy is a secret agent who needs to listen in on their conversation but.

Ataque Man in The Middle (MITM), ¿qué es? Rincón de la Tecnología
A man-in-the-middle-attack is a kind of cyberattack where an unapproved outsider enters into an online correspondence between two users, remains escaped the two parties. The malware that is in the.

Man In The Middle Cyber Attack
A man-in-the-middle (MitM) attack is a type of cyberattack in which communications between two parties is intercepted, often to steal login credentials or personal information, spy on victims.
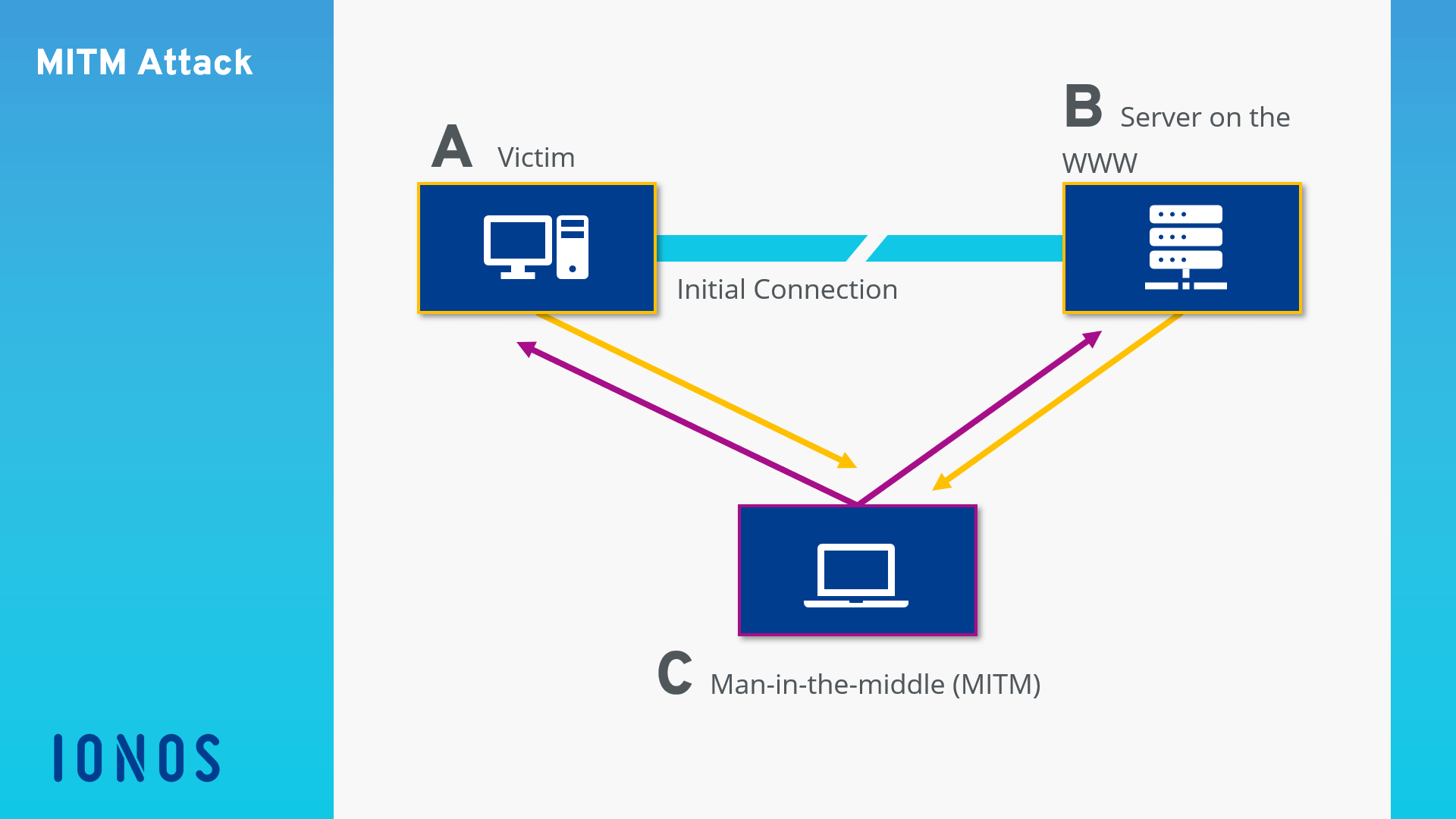
Maninthemiddle attack (MITM) Techniques & Prevention IONOS CA
Cómo prevenir un ataque Man in the Middle. A pesar de las infinitas formas en que estos ataques pueden desarrollarse, en realidad solo hay algunas cosas que se explotan una y otra vez. Para protegerse contra los ataques MitM, existen dos requisitos clave: No repudio: el mensaje proviene de la persona o dispositivo del que dice que proviene.

¿Qué es un ataque ManintheMiddle (MITM)? Definición y prevención
A man-in-the-middle (MITM) attack is a form of cyberattack in which criminals exploiting weak web-based protocols insert themselves between entities in a communication channel to steal data.. None of the parties sending email, texting, or chatting on a video call are aware that an attacker has inserted their presence into the conversation and that the attacker is stealing their data.

Como se proteger de Ataques maninthemiddle (MitM)? Site Defender
Man-in-the-middle (MitM) attacks are a common form of security attack towards wireless networks that allow attackers to catch and manipulate communication between two end devices. One of the advanced MitM attacks is the Multi-Channel MitM (MC-MitM) attack that can manipulate the encrypted network traffic, as presented in ( Vanhoef & Piessens.